Part-Time Module Schedule

Dual Degree
APU-DMU Dual Degree Programme
Accreditation
MORE THAN JUST A CYBER SECURITY MASTER PROGRAMME
Requirements
Entry Requirements
- Bachelor’s degree in Computing or related fields with a minimum CGPA of 2.50, or its equivalent qualification as accepted by the Senate.
- Bachelor’s degree in Computing or related fields with a minimum CGPA of 2.00 and not meeting a CGPA of 2.50 can be accepted, subject to a rigorous internal assessment.
- Bachelor’s degree in non-related fields with a minimum CGPA of 2.00 as accepted by the Senate and with relevant working experience, subject to a rigorous internal assessment.
- Bachelor’s degree in non-related fields with a minimum CGPA of 2.00 as accepted by the Senate and without relevant working experience, subject to passing pre-requisite courses.
°Applicants without a Bachelor’s degree or equivalent in Cyber Security or Forensic Computing must pass the perquisite modules in Cyber Security and Digital Forensics to continue with the Master’s degree.
* Applicants without a Computing-related Bachelor’s degree must pass the pre-requisite modules to continue with the Master’s Degree.
Note: The above entry requirements may differ for specific programmes based on the latest programme standards published by Malaysian Qualifications Agency (MQA).
- IELTS : 5.5
What We Teach
This programme is specifically designed to provide:
- Opportunity for professional development at an advanced level within the area of Cyber Security.
- Enhancement of skills and knowledge in Cyber Security for practising IT professionals.
- Ability to further develop specialisation gained in taught modules through an extensive research-based and/or technical-based dissertation, to prepare the student to be a subject matter expert in the field.
- Furthermore, APU is also poised to become a frontrunner in cyber security research through the establishment of the Forensics and Cyber Security (FSEC) Research Centre, through which research activities will be undertaken to challenge boundaries in the application of cyber security.
-
The Benefits of the Programme
- The curriculum covers a wide range of industry relevant subject areas in Security Operations Centre (SOC) and Incident Response, Security Auditing and Assessment, Advanced Ethical Hacking, E-Investigation, Data Analytics in Cyber Security etc.
- External reviews conducted by Cyber Security Malaysia (CSM), KPMG and F-Secure during the development of the programme curriculum.
- Programme Support by an Industry Advisory Panel involving cyber security experts from Cyber Intelligence, Cyber Test Systems, Akati Consulting Group and Cyber Security Malaysia (CSM).
- A fully-functional Security Operations Centre (SOC) that allows students to have handson cybersecurity operations platform to monitor live data which allows them to perform real-time cyber security monitoring to fortify network defense with global threat intelligence and launching faster response on cyber security incidents.
- A full-fledged Cyber Threats Simulation and Response Centre – Cyber Range is also included within the Cyber Security Talent Zone in APU. Cyber Range incorporates latest technologies and a military grade cyber-defence system, enabling students to understand and formulate defence strategies, and practice the entire chain of cyber defence, while preparing them to deal with real cyber threat attack when it happens.
- A technical project related to Cyber Security as dissertation in the final semester.
- Research opportunities for students via APU’s Forensic and Cyber Security Research Centre - FSEC.
-
Who Should Attend
This programme is geared towards practicing IT/Computing professionals within industry who seek further formal qualifications in Cyber Security. In addition, professionals and managers who wish to enhance themselves with Cyber Security knowledge and skills to postgraduate level will find this programme attractive. Fresh undergraduate students from Cyber Security / Digital Forensics background will also find this programme worthwhile as a path to further enhance their academic qualifications.
-
Modules & Project
This programme comprises 10 coursework modules and a Project. There are 7 compulsory Core Modules (including Research Methodology module) and you will have to choose 3 elective modules from those listed.
Pre-Requisite Modules (for non-computing students)
Duration: 1 month (Full-time) / 4 months (Part-time)
- Cyber Security
- Digital Forensics
- Digital Forensic and Cyber Security Tools
Core Modules- Information Security Design
- Data Analytics in Cyber Security
- Cyber Security & Threats
- Security Operations Center & Incident Response
- Advanced Ethical Hacking
- Advanced Digital Forensics
- Research Methodology in Computing & Engineering
- Project
Elective Modules (Choose 3)*
- Network Design & Performance
- Information Security Architectures
- Security Audit and Assessment
- E-Investigation
- Applied Scripting in Cyber Security
*Elective modules may be pre-selected for students at the beginning of the semester. If students wish to change these pre-selected elective modules, they can choose from the available modules offered in the semester OR among the intensive delivery modules – however such changes may prolong the study duration. -
Project
As part of this course, you are expected to complete an extensive project paper in relation to Cyber Security for both academic and industry purposes. This project paper will be supervised by a member of academic staff as the main supervisor. It may involve working with an external organisation (probably directly relevant to your work or organisation or any of our industry partners). You are given considerable flexibility in choosing any Cyber Security related topics to base your project paper. As for the deliverables, you are required to come up with a prototype/ simulation/ framework etc. (the list is just an example and not limited to only these) and to produce one project paper and a publishable conference/ journal paper consists of summary of the work.
Distinguished
Rocheston
 |  |
 |
The Rocheston Certified Penetration Tester (RCPT) program stresses research, live labs and interactive sessions on emerging security findings, offering the scope for defining the information security requirements while finding options to enhance existing methodology assets. The RCPT certification is designed and embedded as part of Advanced Ethical Hacking module in the Master of Science in Cyber Security programme, to allow the students to have an industry-standard exposure towards penetration testing as well as an opportunity to upskill themselves in real-life scenarios and simulations through the offered CyberLabs. As such, every student in the programme is given equal opportunity in getting their hands on the certification as part of the syllabus learn in the module without the need of taking up additional training resources. Studen can opt for the Rocheston certification which is valid for 2 years and subject to a renewal process to ensure all Penetration Testers are updated with the current scope of Penetration Testing.
Cyber Security Innovation (Education) of the Year award
APU Wins Cyber Security Innovation (Education) of the Year 2024 by CyberSecurity Malaysia

We are thrilled to share the exciting news that APU has been honoured with the prestigious Cyber Security Innovation (Education) of the Year award by CyberSecurity Malaysia at the Malaysia Cyber Security Awards 2024 held at KLCC.


Facilities at APU
The APU Centre Point & Atrium serves as a melting pot of cultures from all over the world. Here, cultural activities are organised regularly at the campus, fostering long-lasting intercultural relationships among APU students, who come from over 130 countries.
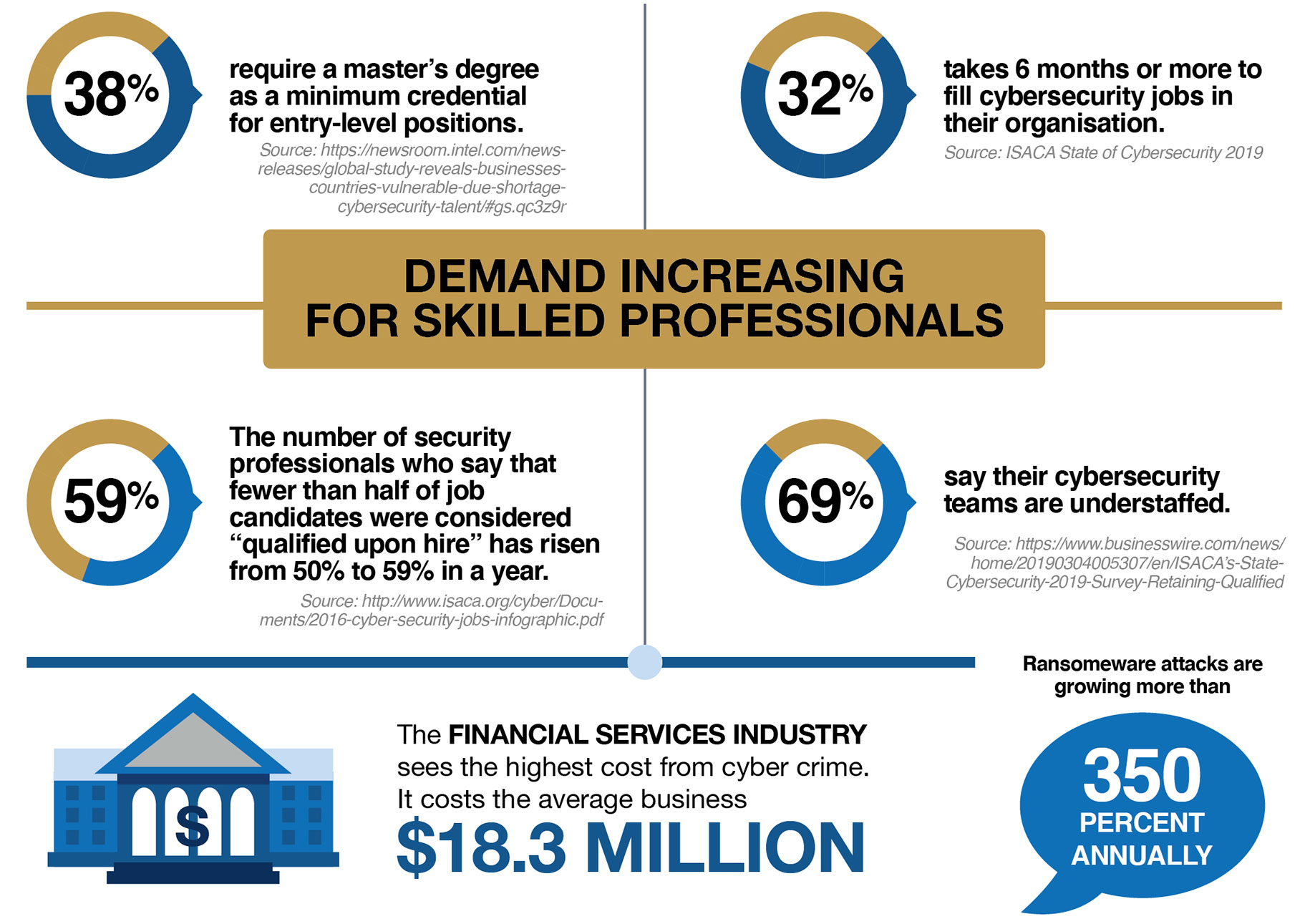
GLOBAL CYBERSECURITY SKILL SHORTAGE + INCREASED BUDGETS =
CAREER OPPORTUNITIES

DEMAND INCREASING FOR SKILLED PROFESSIONALS
“Both the government and the private sector are scrambling for talent. Thousands of information-security jobs are going unfilled as the industry in the U.S. struggles with a shortage of properly trained professionals. By one estimate, there will be 3.5 million unfilled cybersecurity jobs by 2021.”
Source: https://www.securitymagazine.com/articles/90182-the-cybersecurity-talent-gap-an-industry-crisis
Source: https://newsroom.intel.com/news-releases/global-study-reveals-businesses-countries-vulnerable-due-shortage-cybersecurity-talent/#gs.qc3z9r
https://www.businesswire.com/news/home/20190304005307/en/ ISACA%E2%80%99s-State-Cybersecurity-2019-Survey-Retaining-Qualified
https://blogvaronis2.wpengine.com/wp-content/uploads/2018/05/cybersecurity-statistics-2019.jpg
“As digital transformation agendas continue to dominate, a bigger cybersecurity budget is necessary. Almost all companies are looking at technologies such as robotics, machine learning, artificial intelligence, blockchain and so on. All of that change will come with additional cyber risks and necessary investments.”
- Mike Maddison, EY EMEIA Cybersecurity Leader
“Malaysia is one of the top three ASEAN countries that are expected to contribute 75 per cent of cybersecurity services market share by 2025.”
- Gobind Singh Deo, Minister of Communications and Multimedia
Source: https://www.nst.com.my/news/nation/2018/10/418130/ malaysia-expected-contribute-75-cent-cybersecurity-services-market-2025
“Malaysia need 10,500 cybersecurity personnel by 2020.”
- Frost & Sullivan Digital Talent Report
“Organizations were facing difficulties in hiring talents with 32% of these take 6 months or more to fill cybersecurity jobs.”
- Information Systems Audit and Control Association (ISACA) 2019
Ready, Set, Go.
Whether you are locals or traveling here, we have the options for you to pursue your dreams.
RM37,200
Total for Malaysian
RM40,800
(USD9,270)
Total for International
Programme code : (R/0613/7/0019)(05/29)(MQA/FA11934)
All information is correct at the time of publication, but is subject to change in the interest of continuing improvement.

Postgraduate Studies
Learn More
First FinTech Master Programme in Malaysia since 2020
Learn MoreAPEL.C
Online Learning
Facilities
Want to know more ?
Let’s Connect